The Border, Searches and the Digital Devices of Executives and Employees
Reading Time: 2 minutes.

Here’s a story (via @nytimes) about how the border is a back door for device searches.
There is, of course, a “border exception” to the Fourth Amendment, a constitutional doctrine that came of age when national physical borders were also, usually, information-borders as well. Although the discussion in the article takes place in the national-security context, it’s worth American companies giving more careful thought to how they address the way their executives and employees work and travel. Employees usually love using their own devices and storing company data in ways that are readily accessible to and productive for them.
At the border, though, all that corporate data is free game.
As the article notes:
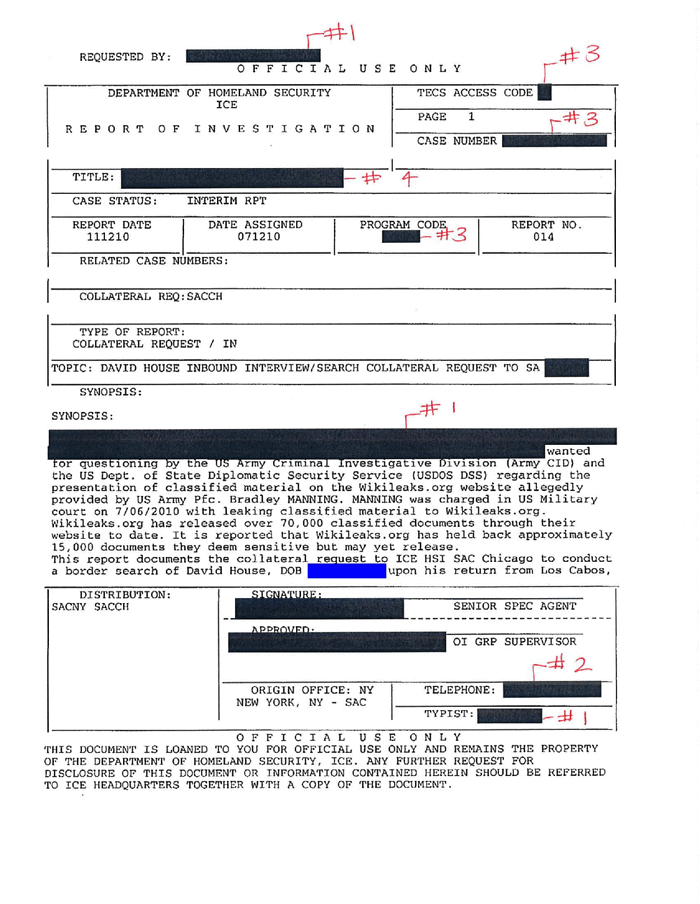
TECS is a computer system used to screen travelers at the border, and includes records from law enforcement, immigration and antiterrorism databases. A report from the Department of Homeland Security about border searches of electronic devices says a traveler may be searched “because he is the subject of, or person-of-interest-in, an ongoing law enforcement investigation and was flagged by a law enforcement ‘lookout’ ” in the Immigration and Customs Enforcement computer system.
For now, the law remains murky about any limits on intrusive border inspections, including how long travelers can be detained, whether they are required to provide passwords for their devices . . . and whether they must answer any question an agent asks. Responses may be recorded in a traveler’s TECS file and shared with other government agencies.
Detention is an inconvenience. To answer (or not answer) an agent’s question is another matter entirely, one that implicates both the company’s legal exposure and the individual’s Fifth Amendment rights.
If you find yourself in a lawsuit or prosecution based on a seizure at the border, it’s worth asking for this document from ICE: